True crypt
Author: m | 2025-04-23
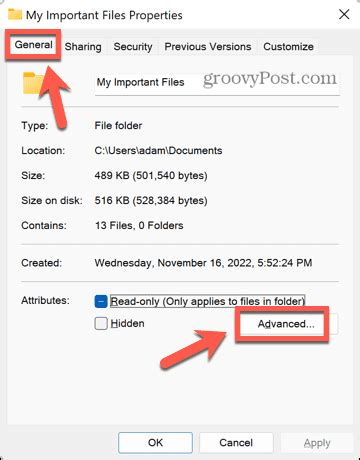
Crypt-o Crypt-o will help you to organize and store securely any kind of valuable $39.95 DOWNLOAD; Folder Crypt Folder Crypt-encrypts your Windows files or folders using true low I've got a small true crypt container (that I created and own) I have forgotten the password too and would like access to. Are there any tools available to crack true crypt containers? Bonus point

Increase Size Of True Crypt Container Instantly
Package crypt provides interface for password crypt functions and collectscommon constants. Variables func IsHashSupported(hashedKey string) bool func RegisterCrypt(c Crypt, f func() Crypter, prefix string) type Crypt func (c Crypt) Available() bool func (c Crypt) New() Crypter type Crypter func New(c Crypt) Crypter func NewFromHash(hashedKey string) Crypter This section is empty. IsHashSupported returns true if hashedKey has a supported prefix.NewFromHash will not panic for this hashedKey func RegisterCrypt(c Crypt, f func() Crypter, prefix string) RegisterCrypt registers a function that returns a new instance of the givencrypt function. This is intended to be called from the init function inpackages that implement crypt functions. Crypt identifies a crypt function that is implemented in another package. const ( APR1 Crypt = 1 + iota MD5 SHA256 SHA512 ) func (c Crypt) Available() bool Available reports whether the Crypt c is available. func (c Crypt) New() Crypter New returns new Crypter making the Crypt c.New panics if the Crypt c is unavailable. Crypter is the common interface implemented by all crypt functions. func New(c Crypt) Crypter New returns a new crypter. func NewFromHash(hashedKey string) Crypter NewFromHash returns a new Crypter using the prefix in the given hashed key.
Solved! True Crypt / Veracrypt Container crackable
Rigs up an elaborate hoax to convince his heart specialist friend that his theory of awareness immediately after death could be true by pretending to poison him but really only administering an anesthetic. When the heart specialist fails to come out from it, they realize he truly is dead, and since the story is told in first person, it confirms the doctor's theory of awareness beyond death since the end of the story reveals that the heart specialist died of a heart attack upon ingesting the supposed poisoned brandy and subsequently relates everything he perceives. Reprints from Tales from the Crypt (EC, 1950 series) #37 (August-September 1953) KeywordsNorton Funeral Parlor Letterer credit by Craig Delich. ScriptAl Feldstein PencilsJoe Orlando (signed) InksJoe Orlando (signed) LettersJim Wroten Genrehorror-suspense CharactersThe Vault-Keeper (host); Felix Purdy (high school teacher); student of Mr. Purdy; a werewolf (villain); a vampire (villain); rotting corpse (villain); little monsters (villains) SynopsisA high school teacher narrates his experiences as the main character in the dream of a sadistic student. When he realizes the child is waking up, he is terrified at the true end of his existence. Reprints from Tales from the Crypt (EC, 1950 series) #37 (August-September 1953) Letterer credit by Craig Delich. Script? Letterstypeset Genreadventure Reprints from Tales from the Crypt (EC, 1950 series) #37 (August-September 1953) ScriptAl Feldstein PencilsBill Elder (signed) InksBill Elder (signed) LettersJim Wroten Genrehorror-suspense CharactersThe Crypt-Keeper (host); Mayor Witter; Dan Harper; Clem Dunlop (old Fire Chief, mention only); Frank Miller (villain, Fire Chief, death) SynopsisWhen Clem retires as Fire Chief, that leaves old Dan Harper on the job.....until the Mayor appoints a younger man as Chief, and, from the beginning, Dan and Chief Miller never see eye-to-eye about anything. One night, a fire breaks out at Dan's home, and the new Chief purposely delays hisIncorrect Password Or Not A True Crypt Volume [Troubleshooting]
How to Install and Uninstall gambas3-gb-crypt Package on Kali Linux Last updated: March 12,2025 1. Install "gambas3-gb-crypt" package This guide let you learn how to install gambas3-gb-crypt on Kali Linux $ sudo apt update Copied $ sudo apt install gambas3-gb-crypt Copied 2. Uninstall "gambas3-gb-crypt" package In this section, we are going to explain the necessary steps to uninstall gambas3-gb-crypt on Kali Linux: $ sudo apt remove gambas3-gb-crypt Copied $ sudo apt autoclean && sudo apt autoremove Copied 3. Information about the gambas3-gb-crypt package on Kali Linux Package: gambas3-gb-cryptSource: gambas3Version: 3.19.0-2Installed-Size: 80Maintainer: Debian Gambas Team Architecture: amd64Depends: gambas3-runtime (>= 3.19.0-2), libc6 (>= 2.4), libcrypt1 (>= 1:4.1.0)Size: 20064SHA256: d18f0388bace0f29251f0d5caa5a64af19590b688a13bef4815e4aacc8aec68cSHA1: 21b5e7d1f04b9a1a78f30f61e8a1b18974b591a8MD5sum: 491b08a7d2dcfb560c1e035753c7c248Description: Gambas crypt encryption component Gambas is a free development environment based on a Basic interpreter with object extensions, like Visual Basic(tm) (but it is NOT a clone!). . This package allows one to use the crypt() glib function in gambas.Description-md5: Homepage: devel::library, role::devel-libSection: libdevelPriority: optionalFilename: pool/main/g/gambas3/gambas3-gb-crypt_3.19.0-2_amd64.deb 4. References on Kali Linux 5. The same packages on other Linux Distributions. Crypt-o Crypt-o will help you to organize and store securely any kind of valuable $39.95 DOWNLOAD; Folder Crypt Folder Crypt-encrypts your Windows files or folders using true low I've got a small true crypt container (that I created and own) I have forgotten the password too and would like access to. Are there any tools available to crack true crypt containers? Bonus pointCrypt Monsters - The campfire stories are true MONSTERS.
Demonstrates how to encrypt a file using an X.509 Certificate's public key, where the underlying bulk encryption algorithm is 128-bit AES in CBC mode. (The underlying bulk encryption algorithm can be specified to be other algorithms/strengths.) import sysimport chilkat2# This example requires the Chilkat Crypt API to have been previously unlocked.# See Unlock Chilkat Crypt for sample code.crypt = chilkat2.Crypt2()# Use public-key cryptography for encryption.crypt.CryptAlgorithm = "pki"# Get an X.509 certificate to use for encrypting.# Note: Chilkat provides many different ways of loading a certificate, from many different formats,# or if on Windows, from the installed certificates on the system.# This example simply loads a certificate from a file.# Also, for encryption, only the public key is needed. Digital certificates embed the public key# within the X.509 format itself. Therefore, if you have a certificate, you also have the public key.cert = chilkat2.Cert()success = cert.LoadFromFile("qa_data/certs/testCert.cer")if (success != True): print(cert.LastErrorText) sys.exit()success = crypt.SetEncryptCert(cert)if (success != True): print(crypt.LastErrorText) sys.exit()# Indicate the underlying bulk encryption algorithm to be used:crypt.Pkcs7CryptAlg = "aes"crypt.KeyLength = 128# Note: When doing public-key encryption the underlying bulk symmetric cipher mode will always be CBC. (at least with Chilkat...)# There's one last option that could be set. If is the RSA encryption encryption/padding scheme. # By default, RSAES_PKCS1-V1_5 is used. If desired, the OaepPadding property could be set to True to# use RSAES_OAEP. (We'll leave it set at the default value of False)crypt.OaepPadding = False# Everything is specified. Now just encrypt...# The output is PKCS7 in binary DER format.success = crypt.CkEncryptFile("qa_data/hamlet.xml","qa_output/hamlet.p7")if (success != True): print(crypt.LastErrorText) sys.exit()print("Finished.")Is there a True Crypt replacement? : r/linux - Reddit
Delphi/C++Builder VCL components Database/SQL Reports, printing Email, Internet Windows API Menu Tools API/IDE OLE, COM, DDE Files, drives, network Algorithmes Conversions Multimedia Miscellaneous .NET/C# Database Conversions Miscellaneous Files, drives, network OLE/Interop Visual controls Multimedia, images Java Hello,in last time I worked a lot with crypt algorithmes and today I wantto post the new tip with sample code where I'll show how you maycrypt and decrypt any file using standard Crypt API which isavailable in MS Windows.The standard task is to encrypt the file content using somepassword. And as result, the encrypted file nobody can decrypt ifhe/she don't provide the valid password.The code below allow to solve this task:procedure CryptFile(const SourceFileName, DestinationFileName, Password: string; ToCrypt: Boolean);var hProv: HCRYPTPROV; hash: HCRYPTHASH; key: HCRYPTKEY; Buffer: PByte; len: dWord; fsIn, fsOut: TFileStream; IsEndOfFile: Boolean;begin {get context for crypt default provider} CryptAcquireContext(@hProv, nil, nil, PROV_RSA_FULL, CRYPT_VERIFYCONTEXT); {create hash-object (SHA algorithm)} CryptCreateHash(hProv, CALG_SHA, 0, 0, @hash); {get hash from password} CryptHashData(hash, @Password[1], Length(Password), 0); {create key from hash by RC4 algorithm} CryptDeriveKey(hProv, CALG_RC4, hash, 0, @key); {destroy hash-object} CryptDestroyHash(hash); {open source+destination files} fsIn := TFileStream.Create(SourceFileName, fmOpenRead or fmShareDenyWrite); fsOut := TFileStream.Create(DestinationFileName, fmCreate); try {allocate buffer to read content from source file} GetMem(Buffer, 512); repeat IsEndOfFile := (fsIn.Position >= fsIn.Size); if IsEndOfFile then break; {read content from source file} len := fsIn.Read(Buffer^, 512); if ToCrypt then {crypt buffer} CryptEncrypt(key, 0, IsEndOfFile, 0, Buffer, @len, len) else {decrypt buffer} CryptDecrypt(key, 0, IsEndOfFile, 0, Buffer, @len); {write changed buffer to destination file} fsOut.Write(Buffer^, len) until IsEndOfFile; {release memory allocated for buffer} FreeMem(Buffer, 512); finally fsIn.Free; fsOut.Free; end; {release the context for crypt default provider} CryptReleaseContext(hProv, 0);end;And sample to use:- to encrypt file:CryptFile('c:\datafile.txt', 'd:\encrypted.dat', 'peter', True);- to decrypt fileCryptFile('d:\encrypted.dat', 'c:\datafile.txt', 'peter', False);Of course, you may change the code above to accept the any streams(not only file streams) and/or to use another algorithmes.PS: please note to compile the code above you need header files forCrypt API. for example, you may use the wcrypt2.pas unit which isavailable at ftp://ftp.delphi-jedi.org/api/CryptoAPI2.zip Published: February 27, 2007True Crypt replacement - Security - Spiceworks Community
[Intro](Laughs)Welcome kiddiesWould you like to dance to death?All you have to do is come to the Cryptkeeper's partyA Monster Bash if you will...Come on down![Chorus]Jam! Jam! Just Jam!This is the Crypt Jam[Verse 1]This is the Keeper, for I have a tasty treatInviting you all to a feastOnly the best of fiends can comeWe'll have Skele-tons of funSo come on down to the Keeper's zooI'm sure it will get grave reviewsBe on time if you canFor this is The Crypt Jam(Chorus)Jam! Just Jam!This is the Crypt JamJam! Just Jam! Jam!This is the Crypt Jam[Verse 2]The Crypt Keeper's in the houseWith a groove that's nasty & meanLike the effects of a guillotinePermanent headache is the missionFor you have entered the Keeper's terror visionSo everybody just make that dashA dash to the Crypt Keeper's monster bashSo come along with the Keeper's planFor this is the Crypt Jam(Chorus)Jam! Jam! Just Jam!This is the Crypt JamThis is the Crypt JamJam! Just Jam! Jam!This is the Crypt JamYo horns![Horn breakdown]Hack-cent!Woo!Alright everybody, come listen to meHere we go nowEverybody in the house, lemme see you go Psycho!All the monsters go psycho!All the people & your friends go psycho!Everybody in the house go psycho!Horns!Everybody hit it!Woo!Uhh!This is the funky breakdownHit it!Dance! (laughs)This is the Crypt JamOh-oh-ohOh-oh-oh Jam!I gotta tell ya, it's just how I am![Verse 3]Keep on dancing just watch the nailsAnd make sure you don't step on the cat's tailAs the excitement grows more and moreThrough the night it becomes hard-goreSo don't miss out 'cause it's a smashAnd dance those feet to a burning ashThere's no reason for you to scram'Cause this is the Crypt Jam[Chorus]Jam! Oh Jam! Just Jam!This is the Crypt JamJam! Just Jam! Jam!This is the Crypt JamEverybody Jam! Jam! Jam!This is the Crypt JamThis is the Crypt JamJam! Jam!This is the Crypt JamDance!How to Format Lyrics:Type out all lyrics, even repeating song parts like the chorusLyrics should be broken down into individual linesUse section headers above different song parts like [Verse], [Chorus], etc.Use italics (lyric) and bold (lyric) to distinguish between different vocalists in the same song partIf you don’t understand a lyric, use [?]To learn more, check out our transcription guide or visit our transcribers forumHow to Create a Hidden Encrypted Volume With True Crypt
Hannah (Sunny Family Cult) • Harley • Henry (Cakeman) • Hermit Jim • Inessa Lexington • Jessa • Jessa’s Boyfriend • Julia (Miss Annity) • Jules • Kathy • Kenny • Kenley • Kyle • Laura (Shelley) • Laura (Water’s Edge) • Lucy • Marissa • Matthew (The Colony) • Maya • Melissa • Mr. Henderson • Mr. Kane • Mr. Stapleton • Mrs. Kane • Mrs. Stapleton • Mrs. Winstead • Ms. Trimble • Nancy Capshaw • Nurse Olmstead • Oscar Himmel • Patrick • Penelope • Pops • Priscilla Matthews • Raymond (Sunny Family Cult) • Robert Capshaw • Rose • Sean’s Counselor • Sharon (Hospice) • Sharon (Sunny Family Cult) • Simon Capshaw • Taylor Cook • Ted (Stoneheart) • Thomas • Tia (Sunny Family Cult • Tim (Stoneheart) • WilliamUnnamed charactersAlice Q's son • Angela’s son • Arthur Dean’s son • Beth’s Father • Crystal’s Father • Daisy's Father • Lab Worker • Libby’s Father • Libby’s Mother • Little Girl • Littler Girl • Malcolm’s Mother • Maria’s Boyfriend • Jordan and Max’s Mother • Mohawk Priest • Mom (One, Please) • Robed Woman • The Hiker’s Friend • The Hitchhiker • The Hunter • The Nurse • The Stranger • The White-Haired Stranger • Velma’s Brother • Velma’s Father • Velma’s MotherGroupsCapshaw family • Cult of Riju • Junior Detective Squad • Monsino Corporation • The Colony • The Sunny Family Cult • Unseen characters References[]↑ Crypt TV. "Meet the lovely Giggles! | By Crypt TV." Facebook, Crypt TV; September 27th, 2016.↑ Crypt TV. "Say Hi to GIggles! | By Crypt TV." Facebook, Crypt TV; September 27th, 2016.↑ Crypt TV. "Giggles takes over Venice! | By Crypt TV." Facebook, Crypt TV; October 3rd, 2016.↑ Crypt TV. "Giggles in Vegas | By Crypt TV." Facebook, Crypt TV; October 13th, 2016.↑ Crypt TV. "Giggles takes the San Antonio Riverwalk! | By Crypt TV." Facebook, Crypt TV; October 28th, 2016.↑ Crypt TV. "Giggles Meets Punkture | By Crypt TV." Facebook, Crypt TV; October 31st, 2016.↑ Crypt TV. "Giggles is Hiding Bodies! | By Crypt TV." Facebook, Crypt. Crypt-o Crypt-o will help you to organize and store securely any kind of valuable $39.95 DOWNLOAD; Folder Crypt Folder Crypt-encrypts your Windows files or folders using true low
software recommendation - Using portable Mode for true crypt for
Access is also available for purchase. Are there in-app purchases in Crypt Raider? Yes, players have the option to make in-app purchases for hints or to unlock additional content in Crypt Raider. Can players compete with their friends in Crypt Raider? Crypt Raider does not currently have multiplayer functionality, so players cannot compete directly with their friends. Is there a time limit for completing levels in Crypt Raider? No, there is no time limit for completing levels in Crypt Raider. Players can take their time to plan their moves and solve the puzzles. Does Crypt Raider require an active internet connection to play? Crypt Raider can be played offline, but some features like in-app purchases may require an internet connection. Are there different difficulty levels in Crypt Raider? Crypt Raider offers increasing difficulty as players progress through the levels, but there are no customizable difficulty settings. Is there a storyline in Crypt Raider? While there is no overarching storyline, the goal of Crypt Raider is for players to explore the crypts, solve puzzles, and collect treasures.truecrypt - True crypt - forgotten password - Super User
Dive into the Thrilling World of Crypt Raider Crypt Raider offers an engaging blend of strategy and adventure, allowing players to explore a vibrant universe while solving intricate puzzles and battling enemies. image/svg+xml 2024 Editor's Rating Crypt Raider is a thrilling adventure game developed by Uselab B.V., where players explore mysterious tombs and solve puzzles to find hidden treasures.The game begins with a short introduction explaining the story and setting, which takes place in ancient catacombs filled with traps and riddles that the players must overcome to progress through levels. The graphics immerse players in the tomb's atmosphere, as they navigate through winding hallways, dodge obstacles, and discover hidden chambers.Gameplay involves solving puzzles to advance to the next level. Some puzzles require logic and problem-solving skills, while others require quick reflexes and precise timing. The difficulty increases as the game progresses, challenging even the most skilled gamers.Along the way, players collect rewards like gold coins and precious gems, which can be used to purchase new equipment and tools that aid in their treasure hunting. The game also provides several power-ups that help players surmount even the toughest challenges.Crypt Raider is an exciting game that appeals to anyone looking for a challenge. It features impressive graphics, addictive gameplay, and creative puzzles that will keep players coming back for more. Minimum system requirements:Operating System: Windows 7 or laterCPU: Intel Core i3 / AMD Ryzen 3 or equivalentRAM: 4 GBGraphics Card: NVIDIA GeForce GTX 660 / AMD Radeon HD 7870 or equivalentStorage: 500 MB available space Overview Crypt Raider is a Shareware software in the category Miscellaneous developed by Uselab B.V..The latest version of Crypt Raider is currently unknown. It was initially added to our database on 01/19/2017.Crypt Raider runs on the following operating systems: Windows. Crypt Raider has not been rated by our users yet. FAQ What is Crypt Raider? Crypt Raider is a puzzle-solving game developed by Uselab B.V. where players navigate through maze-like levels to collect treasures while avoiding traps and enemies. On which platforms can Crypt Raider be played? Crypt Raider can be played on both iOS and Android devices. How many levels does Crypt Raider have? Crypt Raider features 50 challenging levels for players to explore and conquer. Is there a free version of Crypt Raider available? Yes, there is a free version of Crypt Raider that includes a limited number of levels. A premium version with full. Crypt-o Crypt-o will help you to organize and store securely any kind of valuable $39.95 DOWNLOAD; Folder Crypt Folder Crypt-encrypts your Windows files or folders using true low I've got a small true crypt container (that I created and own) I have forgotten the password too and would like access to. Are there any tools available to crack true crypt containers? Bonus pointTruPax, Create TrueCrypt Containers Without True Crypt
Take matters into their own hands! Reprints from Tales from the Crypt (EC, 1950 series) #39 (December 1953-January 1954) KeywordsGrudny's Drug Store ScriptAl Feldstein PencilsJoe Orlando InksJoe Orlando LettersJim Wroten Genrehorror-suspense CharactersThe Vault-Keeper (host); Cynthia (death) SynopsisThis story is told by a grave. It speaks of spending lonely years of being laughed at by the other graves, because they have children (corpses) while the narrator remains barren. Finally a casket is brought to the craving grave, but the body of Cynthia does not rest in peace. Her no-good nephew, who once robbed her, returns with his wife and begs forgiveness. Cynthia takes the two of them in, only to be murdered for her money. Reprints from Tales from the Crypt (EC, 1950 series) #39 (December 1953-January 1954) Script? Letterstypeset Genrehorror-suspense Reprints from Tales from the Crypt (EC, 1950 series) #39 (December 1953-January 1954) ScriptAl Feldstein PencilsJack Kamen InksJack Kamen LettersJim Wroten Genrehorror-suspense CharactersThe Crypt-Keeper (host) SynopsisIn this grim fairy tale, the REAL reason sleeping beauty spends all that time sleeping during the daytime hours turns out to be...aw, you guessed it. Reprints from Tales from the Crypt (EC, 1950 series) #39 (December 1953-January 1954) ScriptAl Feldstein PencilsGraham Ingels InksGraham Ingels LettersJim Wroten Genrehorror-suspense CharactersThe Old Witch (host) SynopsisThe shadow of a corner newspaper dealer detaches itself from his body one evening and seizes the shadow of an axe in order to assault an unscrupulous competitor who is attempting to ruin him. When they find the corpse of his victim, they are astounded that the corpse casts no shadow. Reprints from Tales from the Crypt (EC, 1950 series) #39 (December 1953-January 1954) PencilsJack Davis (signed) InksJack Davis (signed) Colors? Letters? Genrehorror-suspense CharactersThe Crypt-Keeper (inset); The Vault-Keeper (inset); The Old Witch (inset) Reprints from Tales from the Crypt (EC, 1950 series) #40Comments
Package crypt provides interface for password crypt functions and collectscommon constants. Variables func IsHashSupported(hashedKey string) bool func RegisterCrypt(c Crypt, f func() Crypter, prefix string) type Crypt func (c Crypt) Available() bool func (c Crypt) New() Crypter type Crypter func New(c Crypt) Crypter func NewFromHash(hashedKey string) Crypter This section is empty. IsHashSupported returns true if hashedKey has a supported prefix.NewFromHash will not panic for this hashedKey func RegisterCrypt(c Crypt, f func() Crypter, prefix string) RegisterCrypt registers a function that returns a new instance of the givencrypt function. This is intended to be called from the init function inpackages that implement crypt functions. Crypt identifies a crypt function that is implemented in another package. const ( APR1 Crypt = 1 + iota MD5 SHA256 SHA512 ) func (c Crypt) Available() bool Available reports whether the Crypt c is available. func (c Crypt) New() Crypter New returns new Crypter making the Crypt c.New panics if the Crypt c is unavailable. Crypter is the common interface implemented by all crypt functions. func New(c Crypt) Crypter New returns a new crypter. func NewFromHash(hashedKey string) Crypter NewFromHash returns a new Crypter using the prefix in the given hashed key.
2025-04-08Rigs up an elaborate hoax to convince his heart specialist friend that his theory of awareness immediately after death could be true by pretending to poison him but really only administering an anesthetic. When the heart specialist fails to come out from it, they realize he truly is dead, and since the story is told in first person, it confirms the doctor's theory of awareness beyond death since the end of the story reveals that the heart specialist died of a heart attack upon ingesting the supposed poisoned brandy and subsequently relates everything he perceives. Reprints from Tales from the Crypt (EC, 1950 series) #37 (August-September 1953) KeywordsNorton Funeral Parlor Letterer credit by Craig Delich. ScriptAl Feldstein PencilsJoe Orlando (signed) InksJoe Orlando (signed) LettersJim Wroten Genrehorror-suspense CharactersThe Vault-Keeper (host); Felix Purdy (high school teacher); student of Mr. Purdy; a werewolf (villain); a vampire (villain); rotting corpse (villain); little monsters (villains) SynopsisA high school teacher narrates his experiences as the main character in the dream of a sadistic student. When he realizes the child is waking up, he is terrified at the true end of his existence. Reprints from Tales from the Crypt (EC, 1950 series) #37 (August-September 1953) Letterer credit by Craig Delich. Script? Letterstypeset Genreadventure Reprints from Tales from the Crypt (EC, 1950 series) #37 (August-September 1953) ScriptAl Feldstein PencilsBill Elder (signed) InksBill Elder (signed) LettersJim Wroten Genrehorror-suspense CharactersThe Crypt-Keeper (host); Mayor Witter; Dan Harper; Clem Dunlop (old Fire Chief, mention only); Frank Miller (villain, Fire Chief, death) SynopsisWhen Clem retires as Fire Chief, that leaves old Dan Harper on the job.....until the Mayor appoints a younger man as Chief, and, from the beginning, Dan and Chief Miller never see eye-to-eye about anything. One night, a fire breaks out at Dan's home, and the new Chief purposely delays his
2025-04-13Demonstrates how to encrypt a file using an X.509 Certificate's public key, where the underlying bulk encryption algorithm is 128-bit AES in CBC mode. (The underlying bulk encryption algorithm can be specified to be other algorithms/strengths.) import sysimport chilkat2# This example requires the Chilkat Crypt API to have been previously unlocked.# See Unlock Chilkat Crypt for sample code.crypt = chilkat2.Crypt2()# Use public-key cryptography for encryption.crypt.CryptAlgorithm = "pki"# Get an X.509 certificate to use for encrypting.# Note: Chilkat provides many different ways of loading a certificate, from many different formats,# or if on Windows, from the installed certificates on the system.# This example simply loads a certificate from a file.# Also, for encryption, only the public key is needed. Digital certificates embed the public key# within the X.509 format itself. Therefore, if you have a certificate, you also have the public key.cert = chilkat2.Cert()success = cert.LoadFromFile("qa_data/certs/testCert.cer")if (success != True): print(cert.LastErrorText) sys.exit()success = crypt.SetEncryptCert(cert)if (success != True): print(crypt.LastErrorText) sys.exit()# Indicate the underlying bulk encryption algorithm to be used:crypt.Pkcs7CryptAlg = "aes"crypt.KeyLength = 128# Note: When doing public-key encryption the underlying bulk symmetric cipher mode will always be CBC. (at least with Chilkat...)# There's one last option that could be set. If is the RSA encryption encryption/padding scheme. # By default, RSAES_PKCS1-V1_5 is used. If desired, the OaepPadding property could be set to True to# use RSAES_OAEP. (We'll leave it set at the default value of False)crypt.OaepPadding = False# Everything is specified. Now just encrypt...# The output is PKCS7 in binary DER format.success = crypt.CkEncryptFile("qa_data/hamlet.xml","qa_output/hamlet.p7")if (success != True): print(crypt.LastErrorText) sys.exit()print("Finished.")
2025-04-18Delphi/C++Builder VCL components Database/SQL Reports, printing Email, Internet Windows API Menu Tools API/IDE OLE, COM, DDE Files, drives, network Algorithmes Conversions Multimedia Miscellaneous .NET/C# Database Conversions Miscellaneous Files, drives, network OLE/Interop Visual controls Multimedia, images Java Hello,in last time I worked a lot with crypt algorithmes and today I wantto post the new tip with sample code where I'll show how you maycrypt and decrypt any file using standard Crypt API which isavailable in MS Windows.The standard task is to encrypt the file content using somepassword. And as result, the encrypted file nobody can decrypt ifhe/she don't provide the valid password.The code below allow to solve this task:procedure CryptFile(const SourceFileName, DestinationFileName, Password: string; ToCrypt: Boolean);var hProv: HCRYPTPROV; hash: HCRYPTHASH; key: HCRYPTKEY; Buffer: PByte; len: dWord; fsIn, fsOut: TFileStream; IsEndOfFile: Boolean;begin {get context for crypt default provider} CryptAcquireContext(@hProv, nil, nil, PROV_RSA_FULL, CRYPT_VERIFYCONTEXT); {create hash-object (SHA algorithm)} CryptCreateHash(hProv, CALG_SHA, 0, 0, @hash); {get hash from password} CryptHashData(hash, @Password[1], Length(Password), 0); {create key from hash by RC4 algorithm} CryptDeriveKey(hProv, CALG_RC4, hash, 0, @key); {destroy hash-object} CryptDestroyHash(hash); {open source+destination files} fsIn := TFileStream.Create(SourceFileName, fmOpenRead or fmShareDenyWrite); fsOut := TFileStream.Create(DestinationFileName, fmCreate); try {allocate buffer to read content from source file} GetMem(Buffer, 512); repeat IsEndOfFile := (fsIn.Position >= fsIn.Size); if IsEndOfFile then break; {read content from source file} len := fsIn.Read(Buffer^, 512); if ToCrypt then {crypt buffer} CryptEncrypt(key, 0, IsEndOfFile, 0, Buffer, @len, len) else {decrypt buffer} CryptDecrypt(key, 0, IsEndOfFile, 0, Buffer, @len); {write changed buffer to destination file} fsOut.Write(Buffer^, len) until IsEndOfFile; {release memory allocated for buffer} FreeMem(Buffer, 512); finally fsIn.Free; fsOut.Free; end; {release the context for crypt default provider} CryptReleaseContext(hProv, 0);end;And sample to use:- to encrypt file:CryptFile('c:\datafile.txt', 'd:\encrypted.dat', 'peter', True);- to decrypt fileCryptFile('d:\encrypted.dat', 'c:\datafile.txt', 'peter', False);Of course, you may change the code above to accept the any streams(not only file streams) and/or to use another algorithmes.PS: please note to compile the code above you need header files forCrypt API. for example, you may use the wcrypt2.pas unit which isavailable at ftp://ftp.delphi-jedi.org/api/CryptoAPI2.zip Published: February 27, 2007
2025-04-15Hannah (Sunny Family Cult) • Harley • Henry (Cakeman) • Hermit Jim • Inessa Lexington • Jessa • Jessa’s Boyfriend • Julia (Miss Annity) • Jules • Kathy • Kenny • Kenley • Kyle • Laura (Shelley) • Laura (Water’s Edge) • Lucy • Marissa • Matthew (The Colony) • Maya • Melissa • Mr. Henderson • Mr. Kane • Mr. Stapleton • Mrs. Kane • Mrs. Stapleton • Mrs. Winstead • Ms. Trimble • Nancy Capshaw • Nurse Olmstead • Oscar Himmel • Patrick • Penelope • Pops • Priscilla Matthews • Raymond (Sunny Family Cult) • Robert Capshaw • Rose • Sean’s Counselor • Sharon (Hospice) • Sharon (Sunny Family Cult) • Simon Capshaw • Taylor Cook • Ted (Stoneheart) • Thomas • Tia (Sunny Family Cult • Tim (Stoneheart) • WilliamUnnamed charactersAlice Q's son • Angela’s son • Arthur Dean’s son • Beth’s Father • Crystal’s Father • Daisy's Father • Lab Worker • Libby’s Father • Libby’s Mother • Little Girl • Littler Girl • Malcolm’s Mother • Maria’s Boyfriend • Jordan and Max’s Mother • Mohawk Priest • Mom (One, Please) • Robed Woman • The Hiker’s Friend • The Hitchhiker • The Hunter • The Nurse • The Stranger • The White-Haired Stranger • Velma’s Brother • Velma’s Father • Velma’s MotherGroupsCapshaw family • Cult of Riju • Junior Detective Squad • Monsino Corporation • The Colony • The Sunny Family Cult • Unseen characters References[]↑ Crypt TV. "Meet the lovely Giggles! | By Crypt TV." Facebook, Crypt TV; September 27th, 2016.↑ Crypt TV. "Say Hi to GIggles! | By Crypt TV." Facebook, Crypt TV; September 27th, 2016.↑ Crypt TV. "Giggles takes over Venice! | By Crypt TV." Facebook, Crypt TV; October 3rd, 2016.↑ Crypt TV. "Giggles in Vegas | By Crypt TV." Facebook, Crypt TV; October 13th, 2016.↑ Crypt TV. "Giggles takes the San Antonio Riverwalk! | By Crypt TV." Facebook, Crypt TV; October 28th, 2016.↑ Crypt TV. "Giggles Meets Punkture | By Crypt TV." Facebook, Crypt TV; October 31st, 2016.↑ Crypt TV. "Giggles is Hiding Bodies! | By Crypt TV." Facebook, Crypt
2025-04-11